Name: Abhinav Porwal
Profile: Cyber Security Researcher
Email: abhinavporwal@protonmail.com
About me
I am a Cyber Security Analyst and a Hacker with an ethical mindset.
I have experience in web-app security, API security, vulnerability assessment, and penetration testing. I have used tools like Burpsuite, Acunetix, Nessus, Nmap, Pentest Tools, Kali Linux, and some GitHub open source tools like Amas, Aquatone, Subfinder, etc. to find vulnerabilities in web applications.
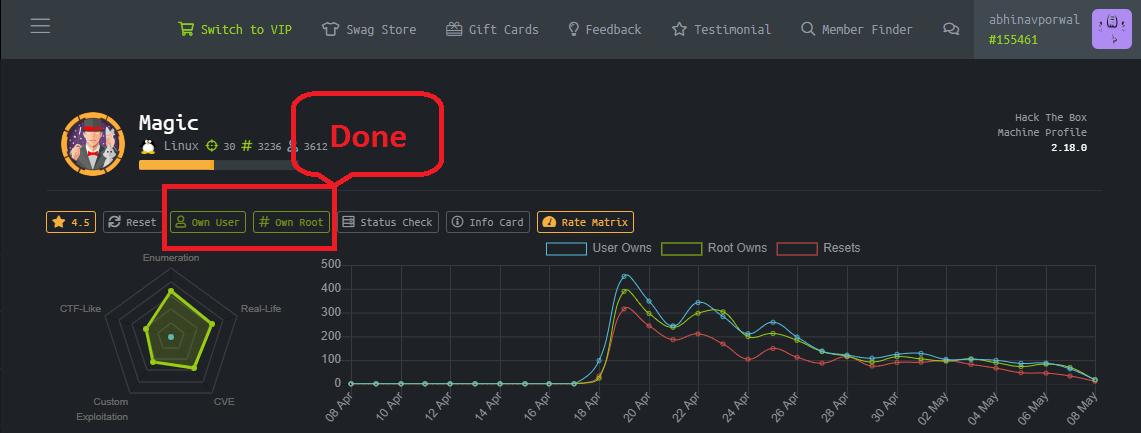
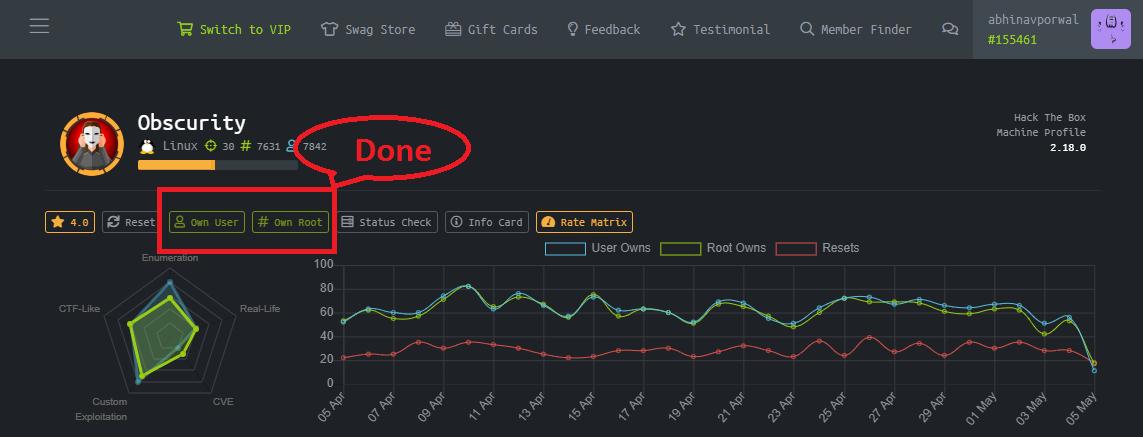
Vulnerabilites acknowledged for : Subdomain Takeover, Sensitive Information Disclosure, Account Takeover, Injection, Privilege Escalation, LFI, XSS, OWASP Top 10, etc. Till now I have secured 200+ companies.
- Your mind is a storage room of information, keep the door locked.
- _ a _ _word is not a PaSSword without Protect, Save and Secure!
- Think before you click.
- Be secured.
Services
What I Do
VAPT
Vulnerability Assessment and Penetration Testing are both security services that focus on identifying vulnerabilities in the network, server and system infrastructure.
Bug Bounty Hunting
Become a bug bounty hunter: A hacker who is paid to find vulnerabilities in software and websites.
Penetration Testing
Penetration testing is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system.
Web Development
Web development is the work involved in developing a web site for the Internet or an intranet.
Graphic Design
Graphic design is the process of visual communication. Designs unique & memorable logos & brand identities.
Digital Marketing
Digital marketing is the marketing of products or services using digital technologies on the Internet, through any digital mediums.
250
WORKS COMPLETED3
YEARS OF EXPERIENCE200
TOTAL CLIENTS280
AWARD WONPortfolio
My Works, Achievements & Swags.
Give your computer a rest when you’re not at your desk.
Lock your computer when away from your desk, it only takes seconds for someone else to do something in your name.
See something wrong? Do something right.
You wouldn't share your ATM pin, so why would you share your password?
Blog
This is a blog that will capture the trends in cyber security & IT technology.
Cyber Security
Introduction of Cyber Security.
Cyber security consists of technologies, processes and controls designed to protect systems, networks, programs, devices and data from cyber attacks. Effective cyber security reduces the risk of cyber attacks and protects against the unauthorised exploitation of systems, networks and technologies.
Ethical Hacking
Hacker's Community
Hey guys today we started hacker's community if any one want to join us please Contact. In this community we work in Bug Bounty, Web Application Testing, Penetration Testing and many more cyber security and ethical hacking programs and give rewards.
Cyber Security
What is Bug Bounty?
A bug bounty program is a deal offered by many websites, organizations and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to security exploits and vulnerabilities.